Hands-On Lab

Now that we have talked about Active Directory and understand the theory of it, let's take a hands-on look. I recommend having basic knowledge in Powershell before trying this lab. We'll be taking a look at the internals of Active Directory by using PowerShell commands to view machines, computers, users, and groups.
Lab Setup -
1.) Deploy the Machine
2.) SSH or RDP into the machine (or use the browser-based instance)
Username: Administrator Password: password123@ Domain: CONTROLLER.local
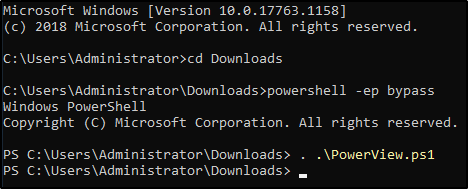
PowerView Setup -
1.) cd Downloads - navigate to the directory PowerView is in
2.) powershell -ep bypass - load a powershell shell with execution policy bypassed
3.) . .\PowerView.ps1 - import the PowerView module
Lab Overview -
I will help you with a few commands the rest is up to you. Use the following cheatsheet here to find what you need. You should have enough knowledge of Active Directory now to investigate the machine's internals on your own.
Example Commands:
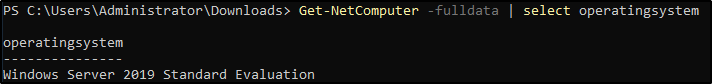
Get-NetComputer -fulldata | select operatingsystem- gets a list of all operating systems on the domain
Get-NetUser | select cn- gets a list of all users on the domain

You can find a cheatsheet for Powerview here by HarmJ0y.
Now you are on your own use the cheatsheet and hints to help you find the rest of the commands and get hands-on with Active Directory.
Deploy the Machine CompletedWhat is the name of the Windows 10 operating system?
What is the second "Admin" name?
Which group has a capital "V" in the group name?
When was the password last set for the SQLService user?
Last updated