Creating Yara rules with yarGen
10.1 Creating Yara rules with yarGen
From the previous section, we realized that we have a file that Loki didn't flag on. At this point, we are unable to run Loki on other web servers because if file 2 exists in any of the webs servers, it will go undetected.
We need to create a Yara rule to detect this specific web shell in our environment. Typically this is what is done in the case of an incident, which is an event that affects/impacts the organization in a negative fashion.
We can manually open the file and attempt to sift through lines upon lines of code to find possible strings that can be used in our newly created Yara rule.
Let's check how many lines this particular file has. You can run the following: strings <file name> | wc -l.
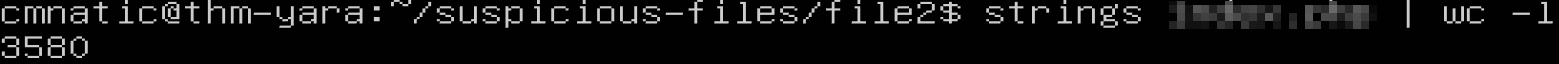
If you try to go through each string, line by line manually, you should quickly realize that this can be a daunting task.
Luckily, we can use yarGen (yes, another tool created by Florian Roth) to aid us with this task.
What is yarGen? yarGen is a generator for YARA rules.
From the README - "The main principle is the creation of yara rules from strings found in malware files while removing all strings that also appear in goodware files. Therefore yarGen includes a big goodware strings and opcode database as ZIP archives that have to be extracted before the first use."
Navigate to the yarGen directory, which is within tools. If you are running yarGen on your own system, you need to update it first by running the following command: python3 yarGen.py --update.

This will update the good-opcodes and good-strings DB's from the online repository. This update will take a few minutes.
Once it has been updated successfully, you'll see the following message at the end of the output.
To use yarGen to generate a Yara rule for file 2, you can run the following command:
python3 yarGen.py -m /home/cmnatic/suspicious-files/file2 --excludegood -o /home/cmnatic/suspicious-files/file2.yar
A brief explanation of the parameters above:
-mis the path to the files you want to generate rules for--excludegoodforce to exclude all goodware strings (these are strings found in legitimate software and can increase false positives)-olocation & name you want to output the Yara rule
If all is well, you should see the following output.

Generally, you would examine the Yara rule and remove any strings that you feel might generate false positives. For this exercise, we will leave the generated Yara rule as is and test to see if Yara will flag file 2 or no.
Note: Another tool created to assist with this is called yarAnalyzer (you guessed it - created by Florian Roth). We will not examine that tool in this room, but you should read up on it, especially if you decide to start creating your own Yara rules.
Further Reading on creating Yara rules and using yarGen:
From within the root of the suspicious files directory, what command would you run to test Yara and your Yara rule against file 2?
Did Yara rule flag file 2? (Yay/Nay)
Copy the Yara rule you created into the Loki signatures directory.
Test the Yara rule with Loki, does it flag file 2? (Yay/Nay)
What is the name of the variable for the string that it matched on?
Inspect the Yara rule, how many strings were generated?
One of the conditions to match on the Yara rule specifies file size. The file has to be less than what amount?
Last updated