Expanding on Yara Rules
6.1. Yara Conditions Continued...
Checking whether or not a file exists isn't all that helpful. After all, we can figure that out for ourselves...Using much better tools for the job. Yara has a few conditions, which I encourage you to read here at your own leisure. However, I'll detail a few below and explain their purpose.
Keyword
Desc
Meta
Strings
Conditions
Weight
6.1.1. MetaThis section of a Yara rule is reserved for descriptive information by the author of the rule. For example, you can use `desc`, short for description, to summarise what your rule checks for. Anything within this section does not influence the rule itself. Similar to commenting code, it is useful to summarise your rule.
6.1.2. Strings
Remember our discussion about strings in Task 2? Well, here we go. You can use strings to search for specific text or hexadecimal in files or programs. For example, say we wanted to search a directory for all files containing "Hello World!", we would create a rule such as below:
 We define the keyword `Strings` where the string that we want to search, i.e., "Hello World!" is stored within the variable
We define the keyword `Strings` where the string that we want to search, i.e., "Hello World!" is stored within the variable $hello_world
Of course, we need a condition here to make the rule valid. In this example, to make this string the condition, we need to use the variable's name. In this case, $hello_world:
 Essentially, if any file has the string "Hello World!" then the rule will match. However, this is literally saying that it will only match if "Hello World!" is found and will not match if "hello world" or "HELLO WORLD."
To solve this, the condition
Essentially, if any file has the string "Hello World!" then the rule will match. However, this is literally saying that it will only match if "Hello World!" is found and will not match if "hello world" or "HELLO WORLD."
To solve this, the condition any of them allows multiple strings to be searched for, like below:
 Now, any file with the strings of:- Hello World!- hello world- HELLO WORLD
Will now trigger the rule.
6.2. Conditions
Now, any file with the strings of:- Hello World!- hello world- HELLO WORLD
Will now trigger the rule.
6.2. Conditions
We have already used the true and any of them condition. Much like regular programming, you can use operators such as:
<= less than or equal to>= more than or equal to!= not equal to
For example, the rule below would do the following:
 The rule will now:
The rule will now:
- Look for the "Hello World!" string - Only say the rule matches if there are less than or equal to ten occurrences of the "Hello World!" string
6.3. Combining keywords
Moreover, you can use keywords such as:andnotor
To combine multiple conditions. Say if you wanted the rule to match if any .txt files with "Hello World!" is found, you can use a rule like below:
 The rule will only match if both conditions are true. To illustrate: below, the rule we created, in this case, did not match because although the file has "Hello World!" it does not have the
The rule will only match if both conditions are true. To illustrate: below, the rule we created, in this case, did not match because although the file has "Hello World!" it does not have the .txt extension:
![]() However, the rule matched this time because the file has both "Hello World!" and the `.txt` extension.
However, the rule matched this time because the file has both "Hello World!" and the `.txt` extension.
 Remembering that the text within the red box is the name of our rule, and the text within the green is the matched file.
Remembering that the text within the red box is the name of our rule, and the text within the green is the matched file.
Anatomy of a Yara Rule
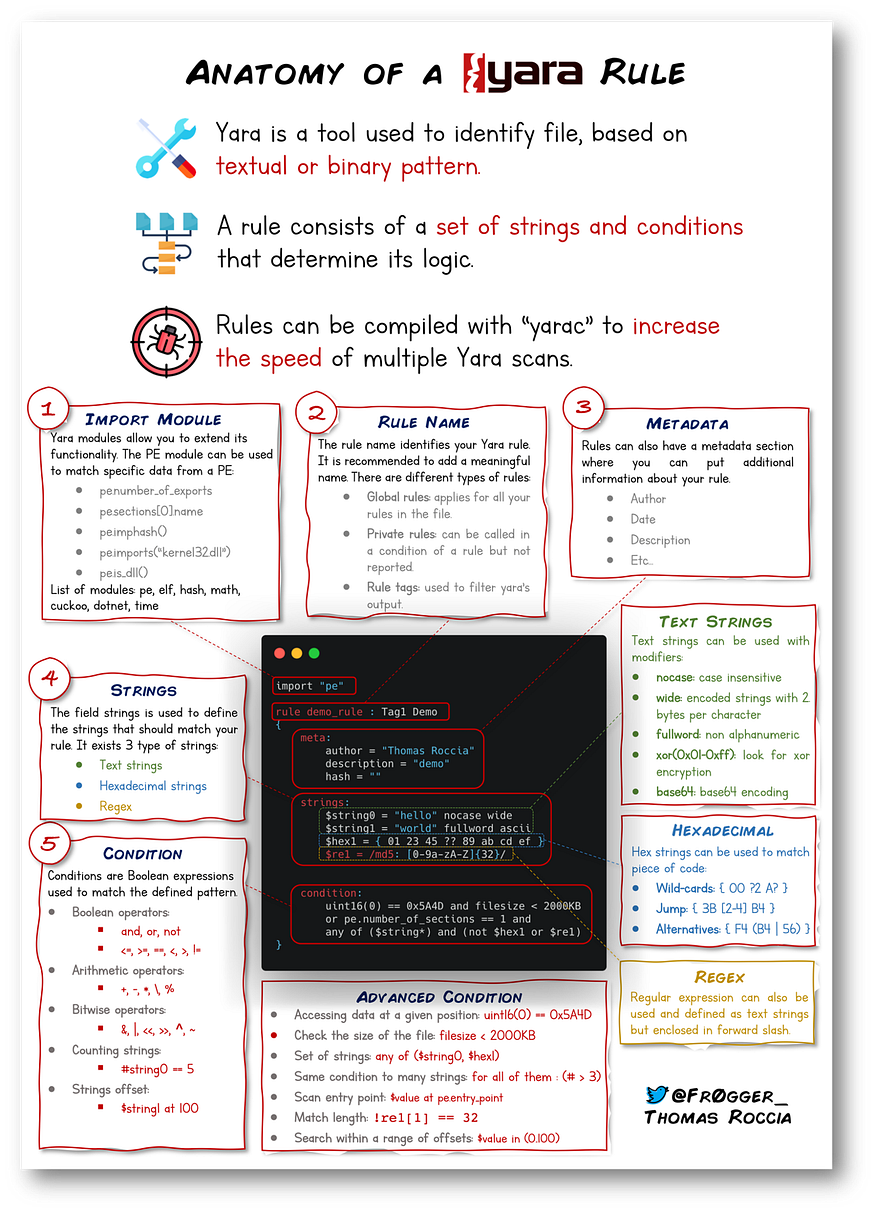
Information security researcher "fr0gger_" has recently created a handy cheatsheet that breaks down and visualises the elements of a YARA rule (shown above, all image credits go to him). It's a great reference point in getting started!
Last updated