Filtering Packets
Packet Filtering is a very important part of packet analysis especially when you have a very large number of packet sometimes even 100,000 plus. In task 3 capture filters were briefly covered however there is a second type of filter that is often thought of as more powerful and easier to use. This second method is known as display captures, you can apply display captures in two ways: through the analyze tab and at the filter bar at the top of the packet capture.
Filtering Operators
Wireshark's filter syntax can be simple to understand making it easy to get a hold of quickly. To get the most out of these filters you need to have a basic understanding of boolean and logic operators.
Wireshark only has a few that you will need to be familiar with:
and - operator: and / &&
or - operator: or / ||
equals - operator: eq / ==
not equal - operator: ne / !=
greater than - operator: gt / >
less than - operator: lt / <
Wireshark also has a few other operators that go beyond the power of normal logical operators. These operators are the contains, matches, and bitwise_and operators. These operators can be very useful when you have a large capture and need to pinpoint a single packet. They are out of scope for this room however I recommend doing your own research, the Wireshark Filtering Documentation can be a great starting point.
Basic Filtering
Filtering gives us a very large scope of what we can do with the packets, because of this there can be a lot of different filtering syntax options. We will only be covering the very basics in this room such as filtering by IP, protocol, etc. for more information on filtering check out the Wireshark filtering documentation.
There is a general syntax to the filter commands however they can be a little silly at times. The basic syntax of Wireshark filters is some kind of service or protocol like ip or tcp, followed by a dot then whatever is being filtered for example an address, MAC, SRC, protocol, etc.
Filtering by IP: The first filter we will look at is ip.addr, this filter will allow you to comb through the traffic and only see packets with a specific IP address contained in those packets, whether it be from the source or destination.
Syntax: ip.addr == <IP Address>

This filter can be handy in practical applications, say when you are threat hunting, and have identified a potentially suspicious host with other tools, you can use Wireshark to further analyze the packets coming from that device.
Filtering by SRC and DST: The second filter will look at is two in one as well as a filter operator: ip.src and ip.dst. These filters allow us to filter the traffic by the source and destination from which the traffic is coming from.
Syntax: ip.src == <SRC IP Address> and ip.dst == <DST IP Address>
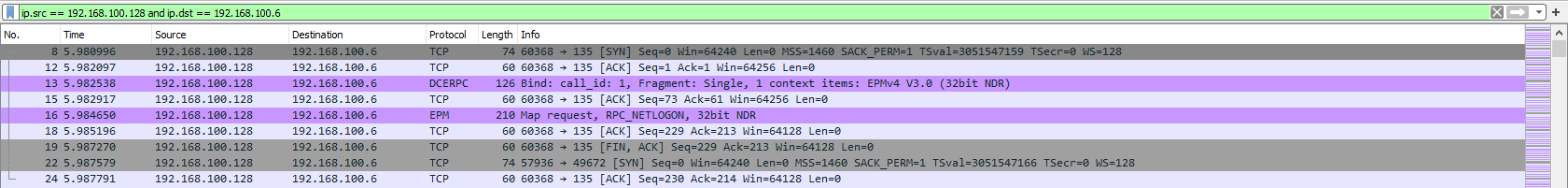
Similar to the first filter we can see that Wireshark is combing through the packets and filtering based on the source and destination we set.
Filtering by TCP Protocols: The last filter that we will be covering is the protocol filter, this allows you to set a port or protocol to filter by and can be handy when trying to keep track of an unusual protocol or port being used.
It is worthwhile to mention that Wireshark can filter by both port numbers as well as protocol names.
Syntax: tcp.port eq <Port #> or <Protocol Name>
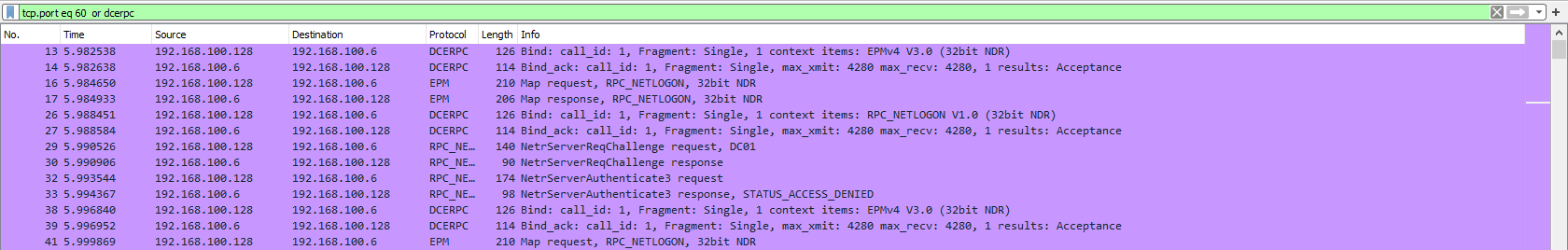
Filtering by UDP Protocols: You can also filter by UDP ports by changing the prefix from tcp to udp
Syntax: udp.port eq <Port #> or <Protocol Name>
That is the end of filtering for this task however I recommend you play around with other filters and operators on your own. Once you're ready move on to Task 5.
Read the above and understand the basics of packet filtering.
Last updated