ICMP Overview
ICMP Overview
ICMP or Internet Control Message Protocol is used to analyze various nodes on a network. This is most commonly used with utilities like ping and traceroute. You should already be familiar with how ICMP works; however, if you need a refresher, read the IETF documentation.
Below you can see a sample of what a ping would look like, we can see a request to the server from ICMP, then a reply from the server.
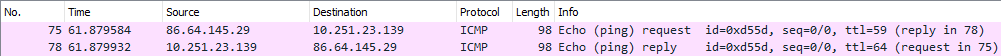
ICMP Traffic Overview
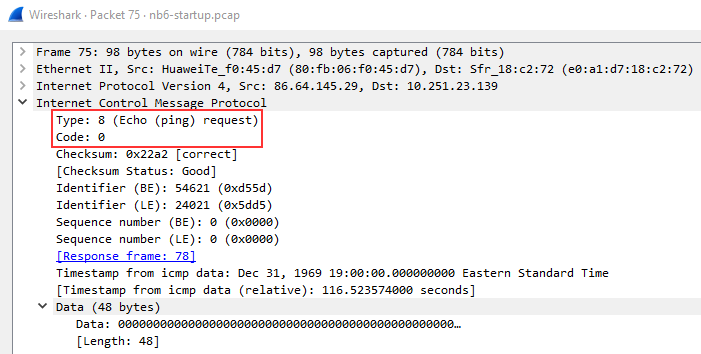
ICMP request:
Below we see packet details for a ping request packet. There are a few important things within the packet details that we can take note of first being the type and code of the packet. A type that equals 8 means that it is a request packet, if it is equal to 0 it is a reply packet. When these codes are altered or do not seem correct that is typically a sign of suspicious activity.
There are two other details within the packet that are useful to analyze: timestamp and data. The timestamp can be useful for identifying the time the ping was requested it can also be useful to identify suspicious activity in some cases. We can also look at the data string which will typically just be a random data string.
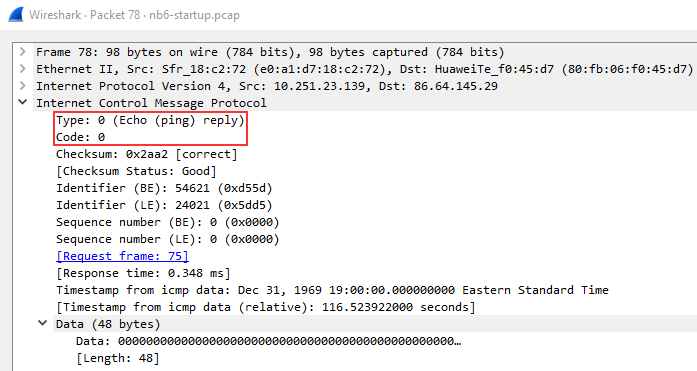
ICMP Reply:
Below you can see that the reply packet is very similar to the request packet. One of the main difference that distinguishes a reply packet is the code, in this case, you can see it is 0, confirming that it is a reply packet.
The same analysis techniques for Request packets apply here as well, again the main difference will be the packet type.
Practical ICMP Packet Analysis
Now that you understand how an ICMP packet is formed and what it contains, we can begin hands-on practical analysis of ICMP packets. Download the provided PCAP or dns+icmp.pcapng.gz from the Wireshark website. This capture only has two protocols so it is up to you whether or not you decide to filter the ICMP protocol or not.
What is the type for packet 4?
What is the type for packet 5?
What is the timestamp for packet 12, only including month day and year?
note: Wireshark bases it’s time off of your devices time zone, if your answer is wrong try one day more or less.
What is the full data string for packet 18?
Last updated